PATCH! PATCH! PATCH!
A proper patch process is crucial as it helps prevent data breaches by fixing security vulnerabilities and bugs. In Samoa, most of the software that we rely on are done outside of the country and its. The more reasons we should manage such software well. It is also the way to make sure all devices run the latest software versions, which implies having access to updated functions and characteristics.
Patch management consists of acquiring, testing, distributing, and installing updates or software patches. It is an essential part of IT Asset Management.
What are the goals of a patch management process?
The objective of patch management is to keep operating systems in a network updated and, therefore, keep them as secure as possible against malware and other vulnerabilities that may result in data losses and significant risks.
1. Reduce interruptions and rollbacks
Planning is crucial to avoid interruptions and rollbacks when deploying updates. A good patch management process implies, among other things, scheduling the updates when the devices are not in use so that the workflow is not interrupted and there are no rollbacks.
2. Create predictability and routine around patching
The patch management process should follow a predictable plan. Routine and prediction are the key elements in the process. Devices and software should be categorized to periodically receive their corresponding patches, with the main aim of preserving information security.
3. Empower IT with emergency powers (rollback and distribution) when needed
Automation is crucial to perform patching effectively, but if, for whatever reason, the automated patch management software fails, then the IT department should be able to perform necessary adjustments.
4. Ensure complete visibility into patch status
It is essential to know how and when each software and operating system has been updated and which patch version all devices have received. A historical report of applied and scheduled patches is crucial to handle this process. Besides, this data should serve to design management reports, allow the IT department to track any problem that might arise, and prove compliance with internal and external standards.
Step-by-step instructions for implementing a patch management process
Organizations generally try to maintain software consistency across the different devices connected to the network and resort to centralized patch management rather than letting each computer download its updates. Information technology requires good handling of the update process to protect all the data stored and exchanged in the network.
Centralized patch management usually implies a software solution that checks missing patches, downloads, and distributes them to the related equipment according to the patch management process defined by the company. These are the necessary steps to illustrate this process:
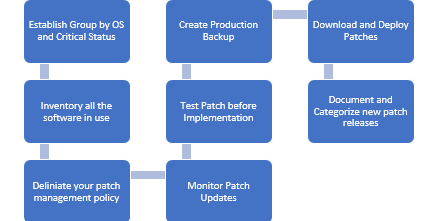
1. Establish device group by OS and critical status
Applications and devices should be categorized according to their risk factor. How critical is that system or device to the organization? What data and processes will be affected? These questions will help determine priorities. Preserving security is crucial.
Servers or computers with confidential data should be considered a high priority and thus should receive patches first. In contrast, less relevant, offline, and rarely used devices should be deemed a low priority.
It is crucial to have a multi-staged approach to streamline the patch management process. In this sense, the IT Manager might also want to establish device groups based on their operating system, as this will facilitate the patching process.
2. Inventory all the software in use
The organization should prepare a comprehensive inventory, including all the operating systems and applications.
A complete inventory is the first step to assessing what patches have been installed and which might be missing. Knowing the current state of patching will help outline the strategy to be developed.
The inventory can be done manually or automatically through asset management software.
3. Delineate your patch management policy
Once priorities have been established based on the critical status of all the devices analyzed, the Patch Management Policy to determine how and when security patches should be deployed.
Patch management policies will specify the procedures to be carried out based on the criticality of devices, the mitigation capabilities, and the risk imposed by the type of security vulnerability identified in each case. This is part of the vulnerability management an organization should carry out.
If, for example, a server with sensitive data from clients requires patching, that should be considered a main priority if that same server needs to be updated to solve two security issues: the patch that mitigates the most dangerous security vulnerability should be deployed first.
4. Monitor patch updates
When patches have been deployed, the IT Division should monitor if they have been installed correctly and that everything is working well. Patch management tools are great for automating this process to do it more efficiently.
Monitoring also implies making sure the policies are being applied correctly. In this sense, the IT staff should evaluate if there is a new patch to be deployed and ensure that the programmed updates, whether daily, weekly or monthly, are being carried out as planned.
5. Test patches before implementation
Best practices require the testing of patches before implementing them because there is a possibility that a patch might cause problems in the systems. Therefore, it is recommended that patches are implemented in a test environment before the actual deployment takes place.
In the haste to solve a security issue, software companies sometimes release buggy patches that introduce problems into environments that are working fine. So, it is always advisable to perform some tests so that the IT team can confirm the patch solves the vulnerability it was designed to address and that it doesn't crash the system or does not introduce any new inconvenience in the network.
6. Create a production backup
After completing the testing in the lab environment, best practice indicates that creating a full backup of all data and configurations set up within the environment, including customizations made to the existing software, is necessary.
7. Download and deploy patches
Once all the previous steps have been completed, it is time to download and deploy patches in a timely manner. Remember, skipping any of the previously mentioned steps is not advisable.
Following a scheme and clear policies is the best way to ensure all the software is updated correctly and that no bugs are introduced into the systems, with all the problems that might imply for the organization.
A patch manager will help ease this process. These solutions include a Windows patch management tool built to automate patches to servers and workstations and other devices to patch different software, such as Linux, macOS, Unix, and other custom software and applications.
8. Document and categorize new patch releases
Once all new patches are downloaded, record and categorize which patches were employed so that information is considered for future reference. This information should be included within security policies and procedures.
It is imperative to document the state of the systems before and after patches have been applied. This will make it easier to handle any future situation that might arise. For example, it will be easier to pinpoint if a problem can be attributed to a buggy patch or missing patch.
Bear in mind that the patch management policy should cover critical and non-critical updates and establish regularly scheduled maintenance periods.

